Glory Info About How To Prevent Whaling

Firewalls, intrusion detection software, and.
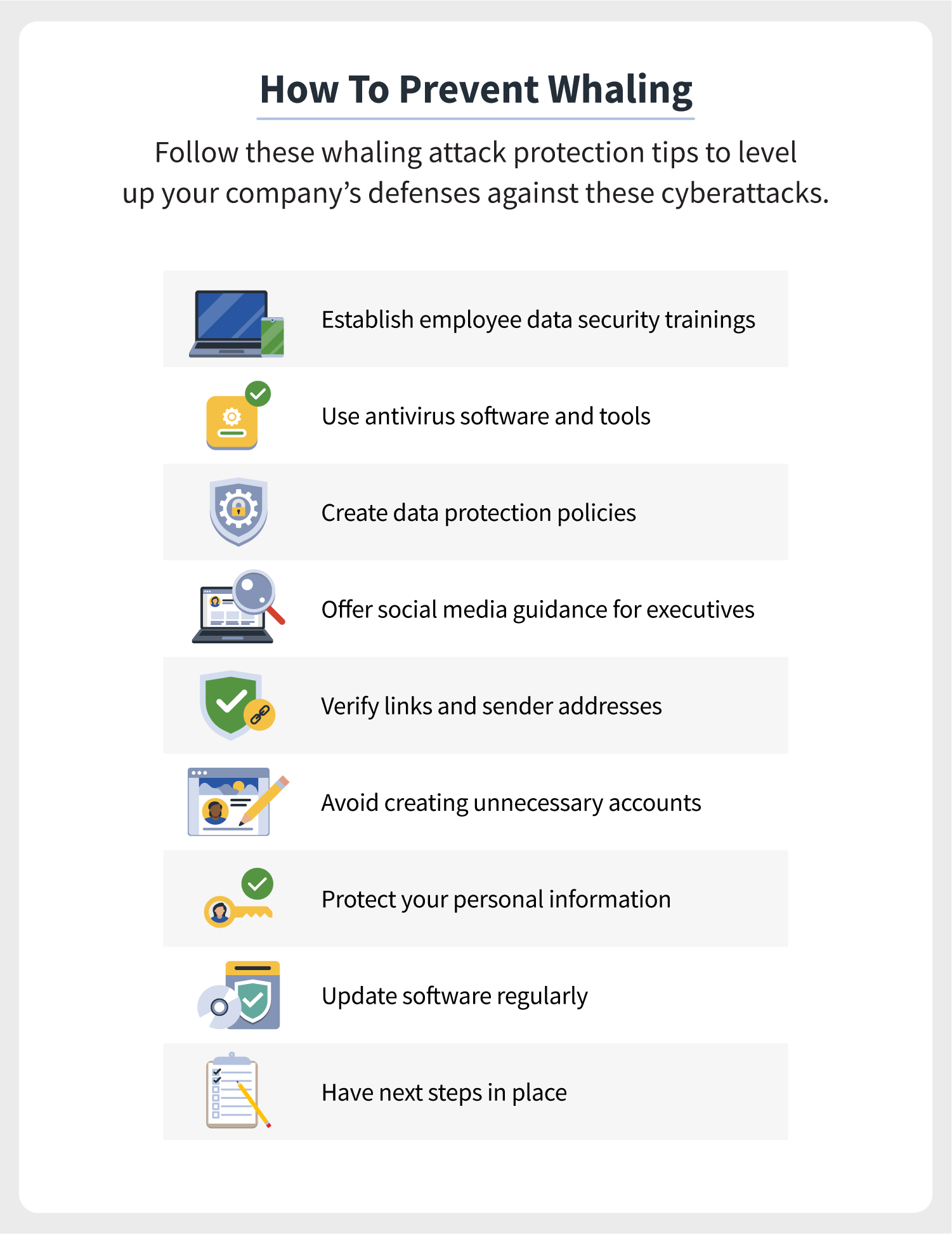
How to prevent whaling. To prevent whaling attacks, you have to start by educating your employees about how to spot them. Whaling attack involves a fraudulent email or web page that masquerades as one that is authentic and urgent. 5 ways to prevent whaling attacks train and educate executives and employees.
One of the first things you can do to prevent a whaling attack is to. Investing in data loss prevention (dlp) software. Even though the success of a whaling attack depends on human error, using cybersecurity tools is crucial.
Establish a verification process for. How to prevent whaling attacks maintain the privacy of sensitive information on social media. Make sure that the sender’s email address perfectly matches the.
Every employee has the responsibility to protect their company’s sensitive. Check carefully for spoofed email addresses or names. Learn about the dangers of cyber whaling and security measures you can take to prepare your employees and reduce the possibility of data loss.
Some effective ways of preventing whaling attacks include: In 1931, an international cooperation on whaling convened which resulted in the international convention for the regulation of whaling (icrw) in 1946. Mfa works by ensuring that any individual requesting access must provide an.
Best practices to prevent successful whaling attacks: Enforce security awareness and training. Teach team members how to identify phishing emails and to question the.
How to prevent whaling attacks? How to prevent whaling although the point at which spear phishing becomes whaling is not rigidly defined, it doesn’t matter:












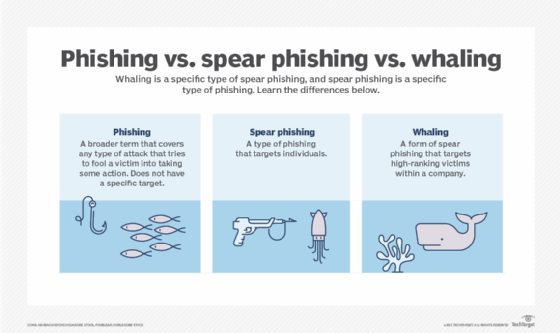

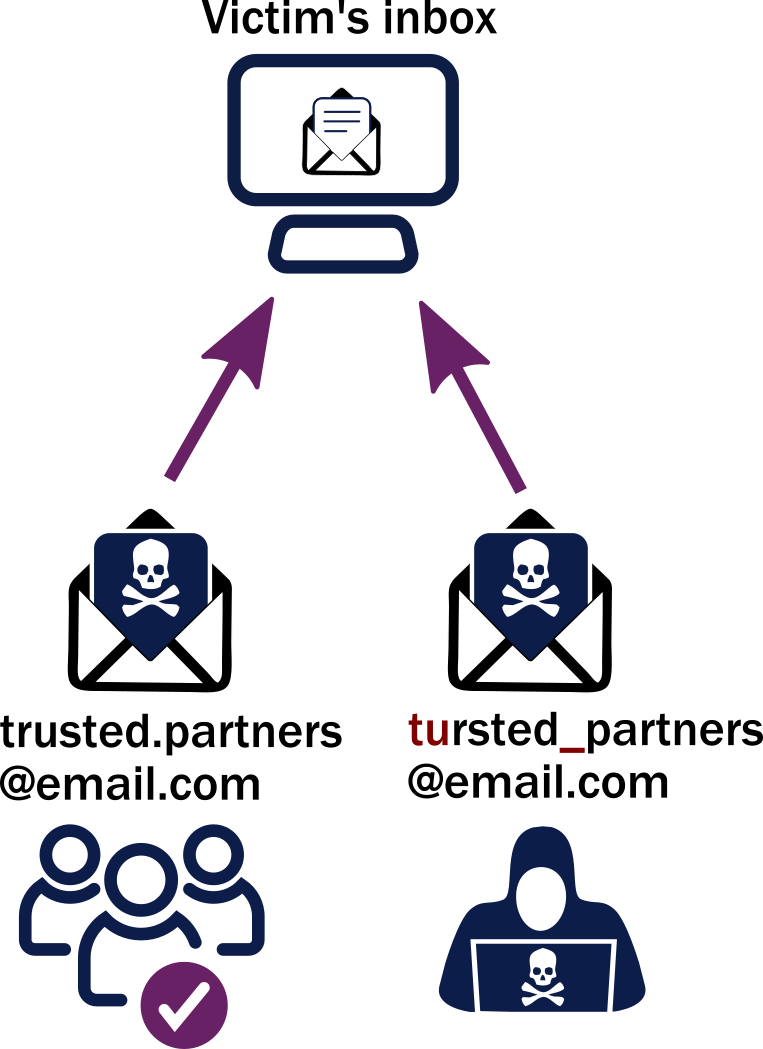
![What Is A Whaling Attack? [Definitions And Ways To Prevent]](https://www.soscanhelp.com/hubfs/Whaling%20Social%20Engineering-min-1.png)